Note: Images are blurred/redacted for confidentiality. They are illustrative and do not disclose any sensitive customer information.
Context
Recently, I came across network data that demonstrates how vulnerable an organization can become when core details are exposed — VLAN layouts, public IPs, device naming and usage patterns. While this may appear harmless, attackers can combine these clues to plan targeted intrusions.
What an Adversary Can Infer
- Map the entire network and identify critical segments like IT, VIP, and finance‑related VLANs.
- Launch targeted attacks such as ransomware or data exfiltration against high‑value assets.
- Perform DoS/DDoS against exposed public IPs to disrupt operations.
- Attempt Man‑in‑the‑Middle interception on poorly secured segments.
Photo Evidence (Redacted)
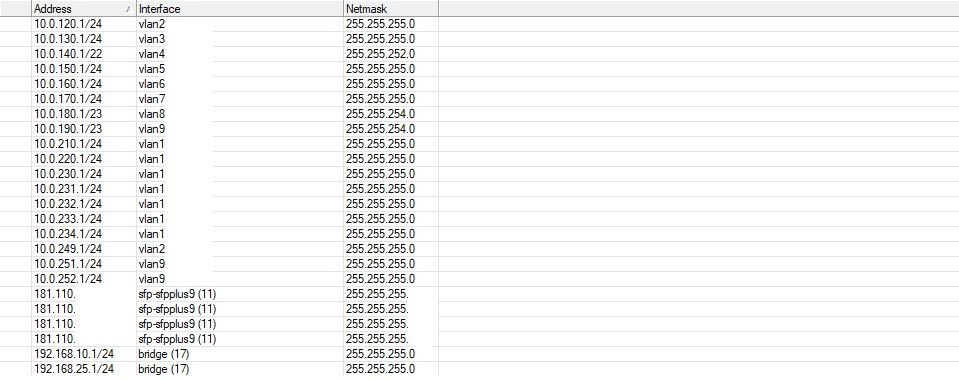
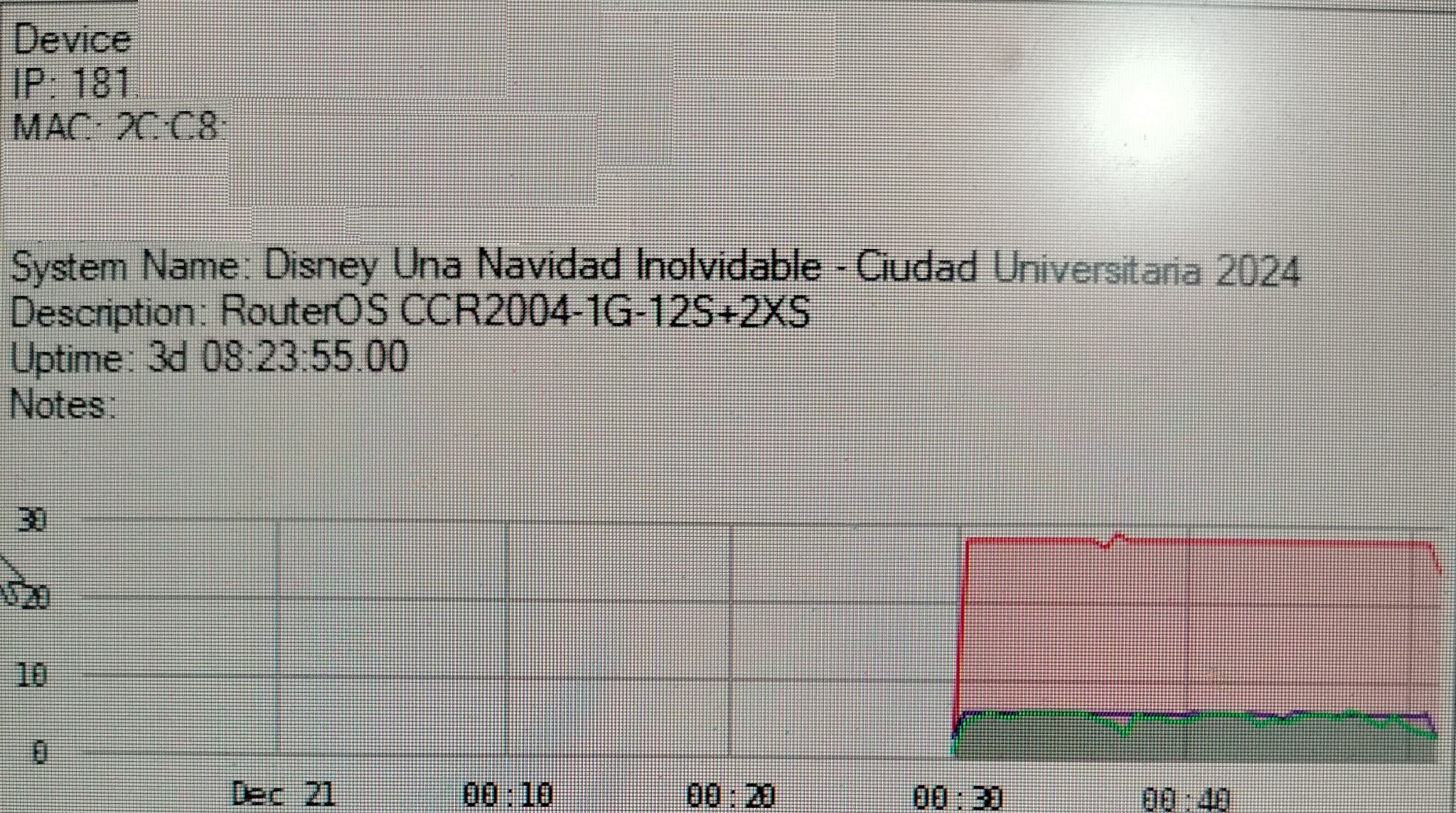
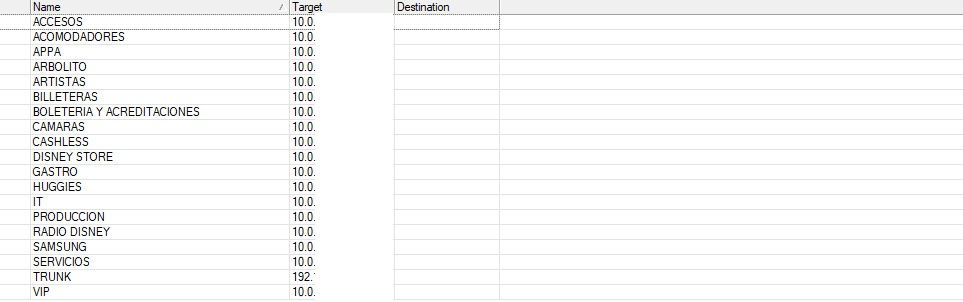
Key Practices for Organizations
- Audit regularly for exposed data and misconfigurations; remove screenshots and docs from public/shared spaces.
- Use strong unique passwords and disable default credentials across all devices.
- Segment networks with strict firewall rules; apply least‑privilege between VLANs.
- Encrypt sensitive traffic; use secure VPNs for remote access (IKEv2/IPsec, WireGuard).
- Keep routers/switches up‑to‑date; apply vendor security advisories promptly.
- Harden management: out‑of‑band admin VLAN, MFA on portals, disable unused services, restrict source IPs.